Skip to: Certificate | Web Browsers | E-Mail Clients
Introduction
Legroom.net uses SSL certificates to secure communications with the site. This helps to ensure that any web traffic and e-mail sent to/through this server is encrypted and protected against snooping. However, as I'm not interested in paying some organization to verify that I am who I say I am, all Legroom.net certificates are self-signed.
What does this mean for you? Two things:
- From an encryption perspective, self-signed certificates are every bit as capable and secure as vendor-signed certificates. This means that, as long as you trust the Legroom.net administrator (see next point for more on this), the certificate itself is fully trustworthy.
- From a trust perspective, self-signed certificates are not validated by an outside party. As a result, web browsers (and other software) consider them to be untrustworthy, and generally throw up pretty nasty warnings along the lines of "OMG UR GIVING UR PASSWORDS TO H4CK3RZ!!1!1!" (give or take a few exclamation points). As noted above, though, the certificate itself is perfectly valid, so as long as you trust the site admin (which would be me), you can trust the certificate.
If you would like to access Legroom.net securely and not have to deal with constant warnings, you can import the Legroom.net CA certificate and instruct your browser/e-mail/etc. to consider it "trusted". Continue reading for more details.
Legroom.net CA Certificate
The Legroom.net CA certificate is the root certificate used to sign all other Legroom.net certificates. By importing and trusting the CA certificate, all certificates that have been signed by that certificate will also be trusted. For example:
- A web server running at www.legroom.net uses a certificate specifically for 'www.legroom.net'
- A mail server running at mail.legroom.net uses a certificate specifically for 'mail.legroom.net'
- Both certificates have been signed by the Legroom.net CA certificate
- By trusting the CA certificate, the www and mail certificates are also automatically trusted, as well as another other certs that have been signed by that same certificate.
The Legroom.net CA certificate can be found here:
http://www.legroom.net/legroom_ca.crt
Details for importing this certificate into common applications can be found below.
Note: Once you have the certificate imported, don't forget to specify https:// when visiting this site; otherwise, your connection will not be encrypted.
Web Browser Installation
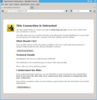
Mozilla Firefox
From within Firefox:
- Click on the above CA certificate link
- When prompted, check "Trust this CA to identify websites." and click OK

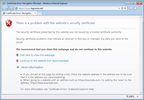
Microsoft Internet Explorer
From within Internet Explorer:
- Click on the above CA certificate link
- When prompted, choose to Open the certificate
- From within the Certificate Information window, click "Install Certificate"
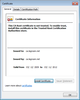
- Click Next. When prompted for the Certificate Store, select "Place all certificates in the following store"
- Click Browse... and select "Trusted Root Certification Authorities"
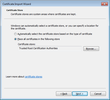
- Click Next until you complete the process, then choose Yes when prompted to install the certificate
E-mail Client Installation
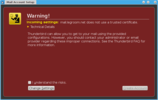
Mozilla Thunderbird
First, you must download the CA certificate from the above link and save it to your computer. To do so, right-click on the link and select "Save Link As..." (or "Save target as..."). Remember where you save it.
Next, from within Thunderbird (you may need to cancel the Mail Account Setup wizard if this is your first time loading Thunderbird):
- Select Tools, Preferences... (or Edit, Preferences... under Linux)
- Select Advanced, Certificates, then click View Certificates
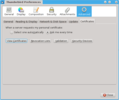
- Select Authorities, then click Import...
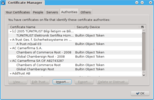
- Navigate to and select the saved certificate
- When prompted, check "Trust this CA to identify websites." and "Trust this CA to identify email users." and click OK

- Click OK